A Business to run successfully has to predetermine the budget based on the strategic business goals, ROI’s, onboarding expert staff, and employee welfare. In the contemporary scenario, Cybersecurity is an addition to it. If you haven’t considered it, then well, you got to!
According to the Cybercrime Magazine, the estimated global damages caused by cybercrimes will cost the world $6 trillion in 2021. They also predict the spending on this segment will upsurge by $1 trillion by this year.
It is alarming for businesses, so they must transform and adopt measures to address these issues.
If you are ready to make time and learn about saving your business from cyber fraud, this guide brings all you need. Gear up to dive into the most common cyber-attacks, principles to follow, and 10 exceptional cybersecurity tips for your business.
4 Types of Cyber-attacks To Be Aware Of!
Fraudsters and hackers may either try to steal your business’s confidential data or crawl into the system or shut it down. These are the two potential objectives behind a security breach. Let us get to it in detail by shedding light on the four most common cyber-attacks on a business (or individual)!
1. Credential Stuffing
Attackers use this type of data breach by stealing your company credentials to log into systems and gain unapproved access. Moreover, with the amplification of automation, this process has gotten a whole lot simpler.
Hackers Conveniently use the credentials present on the large databases to crawl into your system now more than ever. Once they have successfully gained entry, they can misuse your data or carry out monetary transactions as per their intention.
Besides, once they have access to one of your passwords, cybercriminals gain the upper hand on all your business accounts. They can guess the other passwords quite easily, jeopardizing multiple platforms and data entry points.
2. Malware Attacks
Another common type of cyber felony is malware attacks. This type of breach involves a hacker downloading software into your system in stealth mode. Before you realize it, it can steal all the information, manipulate the data, and conduct other unauthorized activities.
Malware can alter your business operations’ functions apart from stealing, deleting, or encrypting your data.Though malware attacks can occur in countless ways, the regular ones include adware, bad bots, ransomware, and trojans.
These may come in the form of fraudulent emails and links, pop-ups, etc. The infected bots can easily collect passwords and use them for the worse. Other types of malware create entry points for attackers to stealthily get inside, require you to pay ransom to regain access.
3. Phishing
Another highly prevalent type of cyber-attack is Phishing which involves sending emails to access personal information. These sources appear to be trustworthy, with attached links or files prompting you to download them. Consequently, you download malware that corrupts your system.
Attackers can also pull off another similar attack — spear phishing that focuses primarily on a single target. In this case, they will first conduct thorough research on a victim and then carry out the scam. Your business email account may get an email that will seem genuine, but it might not be.
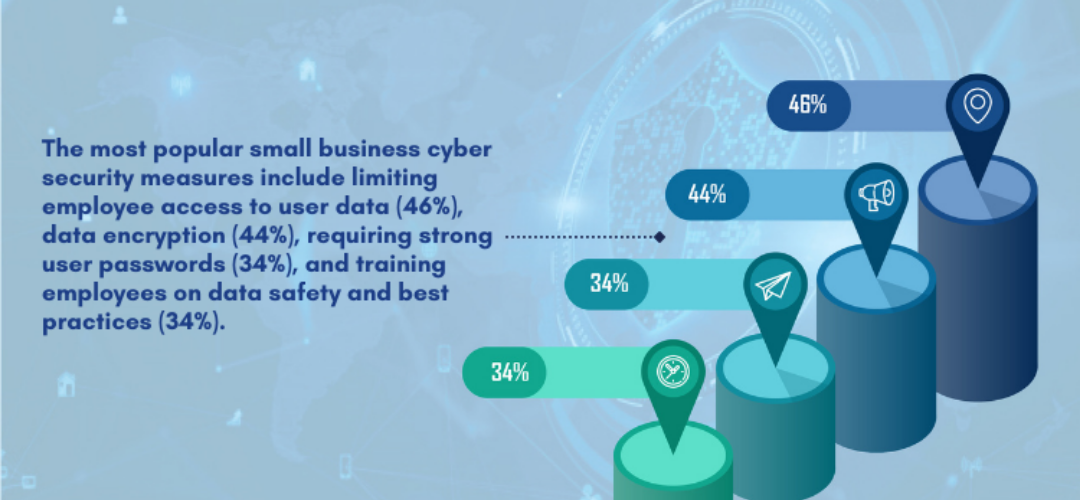
Source:sslstore.com
4. Brute-Force Attack
Brute-Force Attack is a significantly dangerous attack that can affect your entire system. Though this method might take fraudsters a while to crawl into your business account, the disorder is inevitable once they do.
This infallible approach requires attackers to guess the password through the trial-and-error scheme. They use multiple patterns of passwords until they get through. They can then gain access to all of your company’s information, shut down your account, or even corrupt it.
Cyber Security Principles
Now that you have all the tips you need to protect your business accounts from a security breach, here’s how to go about it. These are four categories of guidelines through which you can use the tips mentioned above and prevent cyber breaches!
1. Govern
This category includes the steps that you must take to be precautious before any breaches or thefts occur.
- Your organization has a chief IT security officer looking over and carrying out the cybersecurity department’s activities.
- The details and values of business systems are thoroughly documented.
- You have to identify all of your company systems’ requirements, including those of confidentiality, availability, and integrity.
- Incorporate multiple security risk management techniques and frameworks into the organizational process.
- You need to identify and document security risk management methods before company systems are authorized.
2. Protect
This category includes employing the required security controls to minimize the risk of security breaches.
- Administer and control your business systems in a systematized manner.
- Identify lags and vulnerabilities in the security arrangement and alleviate them in time.
- High-level encryption of company information when being shared or at rest.
- Make back-ups of the entire company database regularly.
- Allow entry only to trustworthy authorities.
3. Detect
With the name being quite self-explanatory, this principle is all about scanning and finding cybersecurity proceedings and breaches.
- Record cybersecurity threats/attacks that have happened in the company so a mitigation plan can be prepared.
- Conduct a thorough analysis of the security activities to detect threats and breaches.
4. Respond
The last guideline talks about how you can react and respond once you identify the potential breach. It also includes recovering from the setback caused due to the intrusion.
- Identify any cyber-attacks and timely report any instances to the respective authorities.
- Prevent the incidents from expanding throughout the system.
- Use business recovery strategies and regularly introduce new ones.
Summing Up
When you learn about ways of controlling and responding to cybersecurity risks, the tips are never sufficient!
The need of the hour is to extend awareness and practice critical techniques to safeguard your systems. Apart from the subscriptions of security applications, VPNs, etc., you have to implement systematized measures and principles to ensure data safety.
If you follow a proactive approach to securing your business practices, it will benefit you internally and externally. Your customers will feel confident about choosing you over your competitors, while you can also safeguard your core progressions.
If you need to know more about IT solutions to overcome any software-related or security issues, Contact us for quick solutions by experts at Desuvit.
Desuvit is a Norway-born software development company delivering Custom Software Development, Mobile Apps, and Web Applications Development for various verticals and business domains. We offer end-to-end solutions for companies with no software or IT division, Startups, and companies that need to scale their software development efforts but lack the expertise required. We help our clients in growing their businesses so we can grow with them. Some of the technologies we work with: .Net, Azure, Microservices, Azure functions(Serverless computing), React Native, Flutter, React JS, TypeScript, Angular, NServiceBus, Azure Service Bus, Azure Queues, SQL Service, MySQL, Cosmos DB, etc.
Enjoyed this article? Subscribe for more valuable and great content !
By subscribing, you agree with our privacy policy and our terms of service.