Security Issues App Developers Need To Deal With While Developing A Mobile App
1. Mobile App Security & it’s Need
2. Impacts of a Low Security Mobile App
2.1 Personal Information Theft
2.2 Financial Information Theft
2.3 App Cloning
2.4 Loss of Revenue
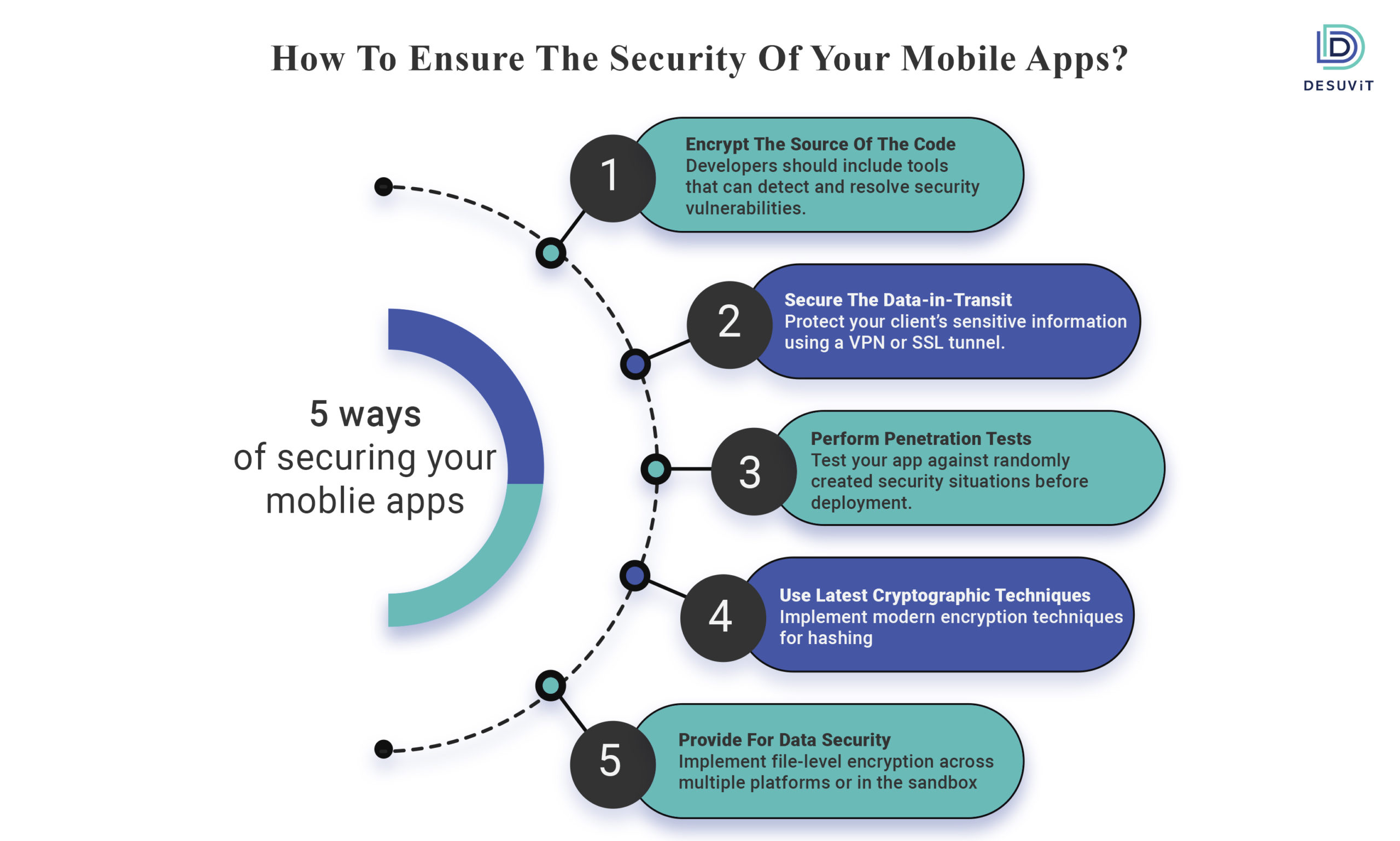
3. ways of Securing your Mobile App
The use of mobile applications is growing day by day. People are becoming more accustomed to connecting with the world from their mobile devices. In the fast-paced life, people do not always have the time to use their desktops or laptops for surfing through the internet or using web applications.
With this rise in mobile app demand, the one thing that developers face is security issues. Technology is a boon and bane at once and hackers are becoming more proficient in hacking different applications.
When developing a mobile app, security is paramount. Check out this guide to learn the different security issues that arise during mobile app development. It also contains certain ways in which developers can prevent these issues.
What Is Mobile App Security And Why Do We Need It?
Before we learn the security issues, let us quickly understand mobile app security and its importance.
Mobile app security is the process through which developers ensure the prevention of digital fraud. Not enhancing the security of mobile applications gives hackers the freedom to steal crucial information about the company and its users.
Developers need to be aware of the issues that can arise and be very informed about the ways to prevent them. Any breach in mobile security can lead to a company losing millions from their business. It also leads to identity theft and harassment for the users.
Now that we know the necessity of mobile app security, let us check out the security issues and preventions.
What Happens When Mobile Security Is Not Strong?
When an app is developed, users believe that the company has taken all measures to secure them. Customers often fill out different personal information depending on the type of app.
If it is a social media app like Facebook or LinkedIn, the customer will provide their personal information like name, address, etc. For financial apps that connect to different banks, the customers will give their financial information.
A study conducted by Symantec Cyber Security showed that almost 1 in 36 smartphones are home to high-risk applications. There has been an upsurge in the number of mobile infections.
This could be attributed to app downloads from unofficial apps, and the presence of these applications in your phone is a threat in itself. Moreover, having low-security apps with malicious apps on your mobile phone is also a way for hackers to access your personal information.
Some common impacts of a low-security mobile app are –
Personal Information Theft
Hacking customer information is not hard once the hacker can get into the application platform. They can access millions of customer data such as banking details, emails, social ids, etc.
Hackers typically send a virus through an unofficial app that asks for permission of your contact list, device location, push notifications, etc. They gather the mobile connection’s IP address and get easy access to the information and files present on the device.
Financial Information Theft
One great way for hackers to get bank details and make transactions is through one-time passwords. Today most banks use a one-time password to allow transactions, but people need to be cautious.
Time and again, many banking Trojans could get access to these details by controlling the user’s SMS. They may send a malicious link in an SMS disguised as some form of banking facility. Once you click that link the virus takes over your phone.
Many famous banks have been affected by different Trojans that breached their app security. According to a press release by Kaspersky, there has been an increase in financial information threats in 2020 using mobile banking Trojans.
App Cloning
A very common scenario that occurs with very famous apps is cloning. This is the way with which hackers breach security and steal customer information. This happens when hackers can steal an app’s codebase.
One known example of this is the cloning of Fortnite Battle Royale. Many users were reported to have downloaded clone apps of Fortnite that were malicious. Google had to put up a notice stating the unavailability of Fortnite on their app store.
Loss Of Revenue
Many applications come with premium features that are a source of revenue for the companies. However, companies often suffer a big loss when hackers can get into their systems and control those premium features.
It does not always happen directly from the parent app itself. Users sometimes use third-party applications for other apps. Even if the hackers can breach the security of the third-party application, they can gain access to all the associated applications linked to the platform.
Problems That Developers Face With Mobile App Security
Research states that the average smartphone user in the US spends approximately four hours on their smartphones every day. In this, 88% of that time is spent using different applications. The same statistics apply to different countries that specify that app usage is on the rise.
App distributors like Windows Store, Apple App Store, Google Play Store, etc., are the place where people could find favorable applications. Companies are opting for mobile apps due to the ease of use and high-reach element.
The top five apps used in the US, according to the latest statistics, are:
- Facebook – 17%
- Instagram – 13%
- Gmail – 9%
- YouTube – 8%
- Twitter – 7%
Let’s look at how the top applications are kept secured and what the developers have to go through during the development stage.
Writing Secure Codes
Developing a mobile application requires coding, and this is one of the most crucial features. If the coding is not strong, hackers can easily breach the application. That is why it is of utmost importance that the coding is very secure while developing the application.
The easiest way to hack is by reverse-engineering the codes. There has been an increase in in-app hacks owing to malicious codes. Therefore, developers need to follow code hardening and code signing when developing their apps.
Code hardening eradicates manual intervention in the coding process. This keeps the app safe from any manual error that can result in security breaches. Making use of agile development strategies for updating the codes after every interval is necessary.
Hard codes are not enough to hold the hackers from breaching your system. Developers need to have manual reviews through which they can detect any automation fails. If there is any use of buffers, developers should notice that the incoming buffer length is not more than the target buffer length.
When using third-party static analysis tools, checking for buffer overflows and memory leaks are necessary. This ensures enhanced safety not just once but repeated times. If you get any issues with buffer overflows and memory leaks, then developers should rectify them first.
Most hacks occur due to these two issues with any other code-related problem. You can also take help from a professional security company that can review the codes and notifies you if there are any vulnerabilities.
Using Libraries Properly
When developing an app, developers often have to make use of third-party libraries. This is a necessity that no developer can avoid. However, there are many scopes of hacking when it comes to third-party libraries. The primary issue that can arise from this is the lack of security.
A good developer will take the codes from the third-party libraries and test them properly. While testing, any codes that are not safe will be detected. The developer will then get rid of the code and search for others that do not put their app security at harm.
There is no ignoring the fact that developers cannot stop the usage of third-party libraries altogether. These codes save a lot of time for the developers. Apart from that, you cannot develop some apps without codes from third-party libraries.
The developer needs to be very cautious while selecting these libraries. It is always better to use popular libraries. Ensure that the author is reliable, and the documentation does not seem to have any missing links.
Developers have to check if the library has a security system. A library that takes security seriously will ensure that the codes used do not lack security. There should also be well-written documentation. Authentic authors and libraries will have detailed documentation that the developers can check.
The main idea is to ensure that the libraries are authentic, and the codes taken are double-checked. This way, there will be no risk of attacks despite using third-party libraries.
Use Of Unauthorized APIs
No app development is complete without the use of APIs. API is an Application Programming Interface that connects two different applications and helps them communicate. Any transaction made on a mobile application is done using APIs. So it is safe to say that having a vulnerable or unauthorized API in the mobile is a serious threat.
Many amateur developers use API without determining their source. It is of utmost importance that the APIs are always taken from authorized sources. Using unauthorized APIs is giving the hackers an open invitation to get access to the data.
The API call is in the form of an API key and the user credential. This comes in the form of access tokens which are similar to cash. This means that if someone has the cash/token or steals it from one else, they can use it for different means.
Attackers can even use bots for making API calls that can compromise business operations and data. This happens when the API in question comes from an unauthorized source and is easy to steal. It happens more in mobile applications since it is present on the device.
If an attacker gets access to the device, it will be very easy to study the app and then manipulate it. As we all know, hacking a device is child’s play in current times with so many unauthorized and open channels on mobiles.
To prevent any of this from happening, developers should always be cautious of the APIs they are using. A small lack in this aspect would cost the company and the users extensively.
Reverse Engineering
Reverse engineering consists of different ways that a hacker can get access to a mobile device. If this happens, the hacker can get any information they need from the device in no time. Reverse engineering informs about the back-end function of the app, the source code modifications, exposes the encryption algorithms, and much more.
Therefore, when reverse engineering occurs, the hacker knows everything a developer has done to establish the app. This gives them the power to use the app process against the developer itself. When this happens, there is a serious risk of information theft that can be very bad for the company and the uses associated with the app.
To prevent reverse engineering, developers need to reduce the functionality given on the client end. It is much safer to increase the functionality on the server end through the web service. After this is done, it becomes much easier for the developer to use hard codes for strengthening the codebase.
We have already learned that an API can be breached using API keys. Just like the data encryption keys, developers should also store the API keys at a safe location. Having the API keys in a location that many people use can be a serious risk.
That is why never store API keys in any location that outsiders can get access to easily. Developers can use private or public key exchange or NDK (Native Development Kit) to store the API key. This way, you prevent reverse engineering and keep your app safe from attackers.
Lack Of High-Level Authentication
Your back-end server of the application is open to hackers if the app’s authorization is poor or missing. Hackers can anonymously take control of the functionalities and get access to any information present in the app. The authentication requirements of any mobile application are mostly different from that of website applications.
When using a mobile app, the person will not be online at all times. However, they remain active in terms that the app can send notifications and alert the user. However, for this offline authentication, there are some additional requirements that you will require.
Offline authentication can pose a serious security threat. To reduce the threat, developers need to implement high-level authentication schemes. It is through these schemes that the developer can strengthen the security. Moreover, several high-privilege attacks can breach the security of a mobile device.
Proper authentication can be done in multiple ways so that mobile security is increased. Any of the authentication requests need to be done on the server end. Once the authentication completes successfully, the developer can load the data into the device. This will ensure that the data does not fall into the wrong hands.
Using multi-factor authentication is necessary for validating the identity of the user. This can be established by putting up security questions, one-time passwords, and many more. Another way to authenticate securely is to encrypt the data and then extract the user credentials. This is necessary when you need to get access to client data storage.
Session Management
A very important feature in mobile application development is session management. This helps the user to retrieve their data if the device gets stolen or lost. Session handling on mobile apps needs to be done very cautiously. This is because the session timing on mobile applications happens for longer than web sessions.
Session management helps the user interact with the mobile application. The communication is done using HTTP, a stateless protocol. There are two basic types of session management which are URL rewriting and cookies. You can use these sessions separately or together. Developers need to keep an eye on these sessions.
When a user logs into the mobile app, the session starts and is known as session hijacking. Attackers can easily hack into the system during this point if the sessions are not taken care of. They can do this by sending malicious links that will steal the cookie files of the app. It can also occur by stealing the algorithms for deriving the session ID.
Applications also need to have a remote log off and sign off so that the data is saved on the stolen or lost devices. This way, anyone who has stolen the device will not get access to the data easily. The user can remotely delete any data saved on the device.
Most of the preventions related to session management are mostly done from the client-side. A software update is also a necessary process of this management. Developers can use ID monitors and VPN that will ensure that no unauthorized access occurs.
Data Encryption
Encryption is the way where developers turn data in an encrypted form. People can only read this encrypted form if it is translated to the original form. This translation can be done with a secret decryption key. Poor data encryption gives open access to the attackers to steal the data.
If the app has poor encryption, then customer and company data will be lost in no time. Developers generally put quite strong encryption in the applications. However, the real issue does not lie in the implementation of the data. It lies in the way that the developers handle the keys.
If the keys are not secured, even the strongest data encryption algorithms will not secure the app. Developers should never store the encryption keys in any file or database that is insecure and can be handled by many.
Hackers go the other way where they do not target the encryption itself but the keys. This becomes easy for them to get the key and translate the data without any major issues.
Using multi-factor encryption is a great way to create obstacles for hackers. Recent data from Thycotic confirms that about 30.68% of the black hat hackers have stated that multi-factor encryption makes it hard to hack into the system.
Multiple layers of encryption are like having multiple doors to the money vault. Even if the hacker can break one layer, they will not pass through the other layers easily. Moreover, the keys of the layers need to be stored in a very secure place.
Insufficient Cryptography
Cryptography is the process through which communications and information are protected using codes. This is done so that only people who are authorized to read the information can do that. If there are any malicious adversaries or third parties, cryptography helps in keeping the data safe.
Cryptography uses encryption that consists of a key that can transform the input and an algorithm. From this, developers get an encrypted output, which ensures that only the person with the encryption can read the information. A security breach occurs when cryptography is insecure.
For developing a strong app, you would require to use strong techniques and tools for cryptography. If your encryption keys fall into the wrong hands, it could damage the company and the user. There is no use keeping the keys in a place that any person can access.
We have spoken about this in the earlier section for both encryption keys and API keys. Any keys necessary for the security of the applications need to be stored securely. Inexperienced developers often make this mistake.
Using two-factor authentication for this process is also necessary. However, make sure you use strong services for the multiple layers. Using SMS as one of the layers is not a suitable process since attackers can hack SMS easily.
Tamper Detection Techniques
Developers need to be aware when someone tampers with their systems and codes. System breaching is something that will occur 9 out of 10 times these days. So developers need to be ready for the “when” and not think about “if.” If developers are ready to prevent breaching, then they can take control of the situation.
To prevent breaches on time, the developers need to be aware on time. For this, there have to be techniques that can make the developers know when the breach happens. Some very common signs that let a developer know that a breach may be taking place. Some of these signs are random restarts, random downloads, and others.
If proper techniques are in place, then the system will directly inform about a breach taking place. This gives the developers the upper hand to prevent the breach from occurring and taking back control of the app.
There is stealth spyware that is not easily detectable, making it harder for the developer to prevent. The first thing developers need to do when a confirmed breach has happened is to take care of the crypto assets. Any other security process can be done later, but the keys need to be secured.
It is always important that the developer should not use the breach’s device to handle the breach. They should use any secure device to open one new wallet and transfer the crypto assets to the new address. When the crypto assets are transferred, the breach intensity already lowers to a great extent.
During the breach, attackers can send malicious codes to the application. If the developer keeps a log of all the code changes, then it would become tough.
Absence Of Proper Testing
Your app is never fully secure, and this is something that developers need to remember. One major aspect of security and finding faults with the app is repeated testing. Testing needs to be done for every small change that occurs in the application. Even if there are multiple changes within a short span, the developers should test the app repeatedly.
Technology is changing fast every day, and so are the security trends. To stay updated and use the latest security services, companies need to use them in the application. For each time a change is made, the developer will have to test the app for security. This provides enhanced protection to your application.
The use of penetration tests and emulators is a great way of identifying the vulnerabilities present in the mobile app. Use security patches in the mobile application along with any new version or update. This will keep the pp secured in case any malicious link attacks the user’s device.
Multiple testing can even detect any security breach that you need to immediately take care of. This saves the company and the user from being attacked by hackers.
Final Thoughts
Knowing about every security risk is not easy. Every day there are new risks that emerge with the advancement in technology. However, the ones mentioned in the guide are some of the basic risks that developers can come across.
The idea here is to make people aware of the risks present and the importance of preventing them. This is especially important for new businesses that are trying to make their name using mobile applications.
A breach in their security will immensely affect their customer base or revenue and their brand name. With so many applications available, users will search for security and move to similar brands that offer them the same.
If you consider hiring a professional mobile app development company that ensures high security, then Desuvit is the one for you. At Desuvit, we develop personalized apps with fully secured solutions. Contact us to get more information about our mobile app development service.
Desuvit is a Norway-born software development company delivering Custom Software Development, Mobile Apps, and Web Applications Development for various verticals and business domains. We offer end-to-end solutions for companies with no software or IT division, Startups, and companies that need to scale their software development efforts but lack the expertise required. We help our clients in growing their businesses so we can grow with them. Some of the technologies we work with: .Net, Azure, Microservices, Azure functions(Serverless computing), React Native, Flutter, React JS, TypeScript, Angular, NServiceBus, Azure Service Bus, Azure Queues, SQL Service, MySQL, Cosmos DB, etc.
Enjoyed this article? Subscribe for more valuable and great content !
By subscribing, you agree with our privacy policy and our terms of service.